It is known that China has a strong economical relation with Ethiopia. However, it is unknown why a piece of malware signed with a VeriSign certificate from a Chinese firm calls back to an Ethiopian command and control server.
Security researchers from Norman have stumbled upon this curious-looking malware, which, at the time was signed by a valid certificate.
After analyzing it, the experts have found that even though the malicious element has been making the rounds only in Ethiopia and its command and control server is located in the same country, the malware itself appears to be Chinese.
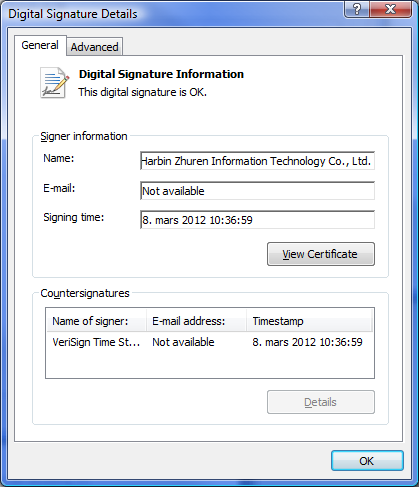
That’s not only because the certificate that signs it is from a Chinese company, Harbin Zhuren Information Technology Co., Ltd., but also due to the fact that the build language ID corresponds with Chinese.
“So what is a Chinese signed malware doing in Ethiopia, calling back to an Ethiopian IP? We can only speculate about this, since we unfortunately do not know the delivery mechanism of the malware. Nor do we know who (if any) have been affected by it, but it makes sense to assume that the target is located in Ethiopia itself,” Snorre Fagerland, principal security researcher at Norman wrote.
During its analysis, the expert found that the malware installs itself as a SafeBoot alternate shell, which is not common for such threats.
After that, it doesn’t immediately step into play. Initially it only creates an “explorer.exe” process to avoid raising any suspicion, being programmed to connect to the C&C server and download other elements only after it’s run using the /r switch.
Symantec was notified regarding the fact that one of its certificates was used to sign malware and the security firm revoked it on March 17. Norman also reported the presence of the threat to the Ethiopian Information Network Security Agency (INSA).
softpedia.com
Niciun comentariu:
Trimiteți un comentariu